Published on
April 17, 2024
As you might have heard, current cryptographic algorithms are going to be obsoleted in the near future. Hence the need to enable post-quantum cryptography operations in tasks involving these algorithms.
One prominent cryptographic task involved in TLS secure communications is called key exchange. In this operation, a key to be used further in encrypting communications is exchanged between your web browser and the web server you're connecting to.
Fortunately, modern web browsers already support post-quantum cryptography for key exchange, though that needs to be enabled in the browsers. This article will drive you through enabling it in most browsers.
Google Chrome and Microsoft Edge
To enable secure, post-quantum hybrid key exchange support in Google Chrome or Microsoft Edge, follow these steps:
Want to implement these PKI practices?
Get expert guidance on implementing secure PKI solutions for your organization.
Get Expert HelpType chrome://flags in the URL bar
Type "kyber" in the search bar
Enable all options (one or two options depending on your browser) using the button on the right
You will then need to restart your web browser to activate this feature.
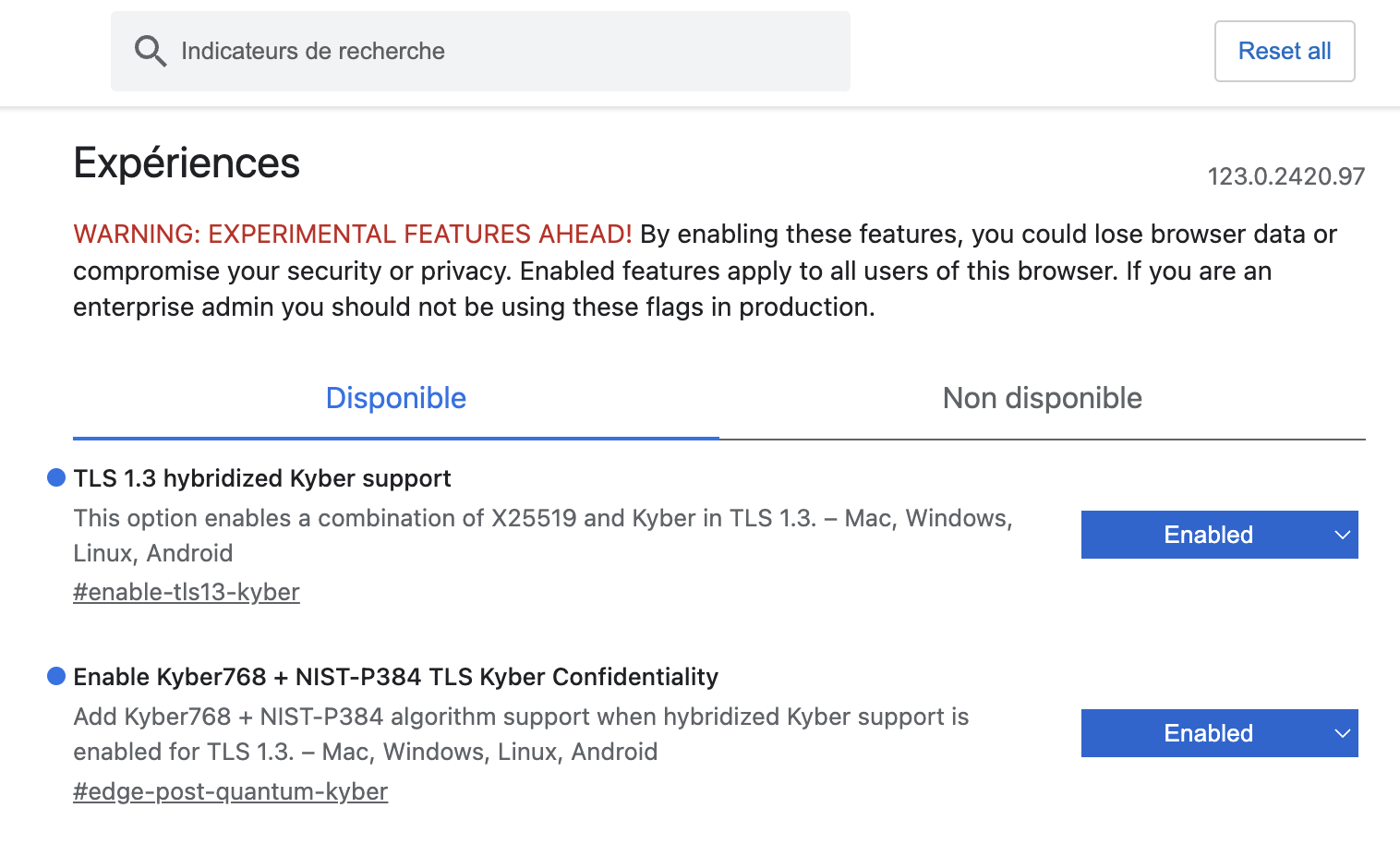 How to enable Post-Quantum Cryptography key exchange support in Chrome and Edge
How to enable Post-Quantum Cryptography key exchange support in Chrome and Edge
Note: you might need to disable the experimental QUIC protocol support in chrome://flags#enable-quic
Mozilla Firefox
To enable secure, post-quantum hybrid key exchange support in Mozilla Firefox, follow these steps:
Type about:config in the URL bar
Type "security.tls.enable_kyber" in the search bar
Enable the option as a boolean
You will then need to restart your web browser to activate this feature.
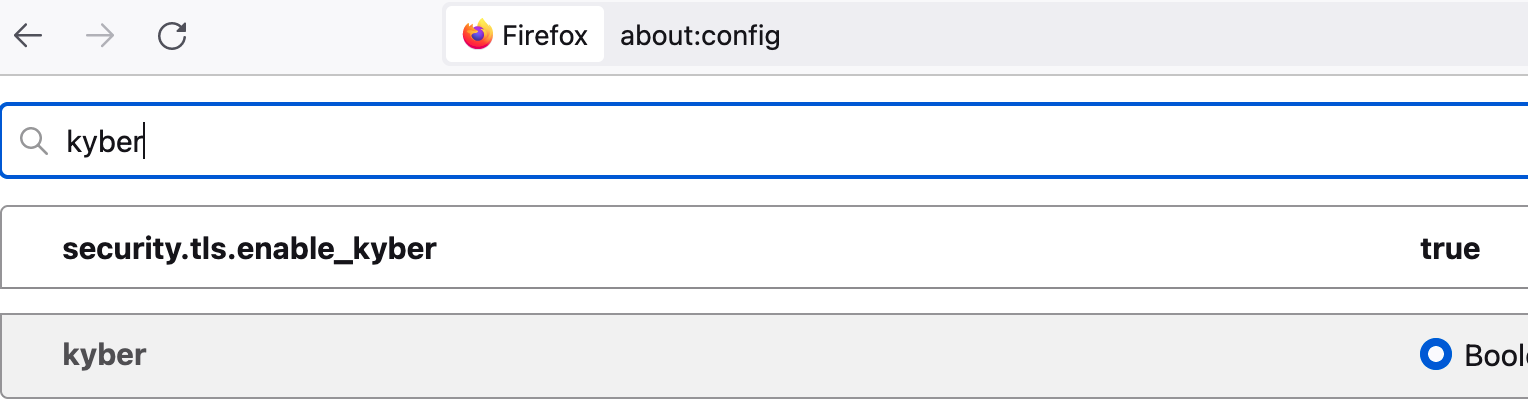 How to enable Post-Quantum Cryptography key exchange support in Firefox
How to enable Post-Quantum Cryptography key exchange support in Firefox
Note: Support within Apple Safari is yet to be announced.