
In today's digital landscape, protecting web applications from potential threats is paramount. As more and more businesses and organizations rely on web servers to deliver their services, the need to protect sensitive data exchanged between clients and servers is becoming more and more pressing.
Transport Layer Security (TLS) provides a robust framework for ensuring the confidentiality and integrity of this data, protecting it from eavesdropping and tampering. For those using Apache Tomcat as a web server on UNIX systems, implementing TLS is not just a best practice, but a necessity.
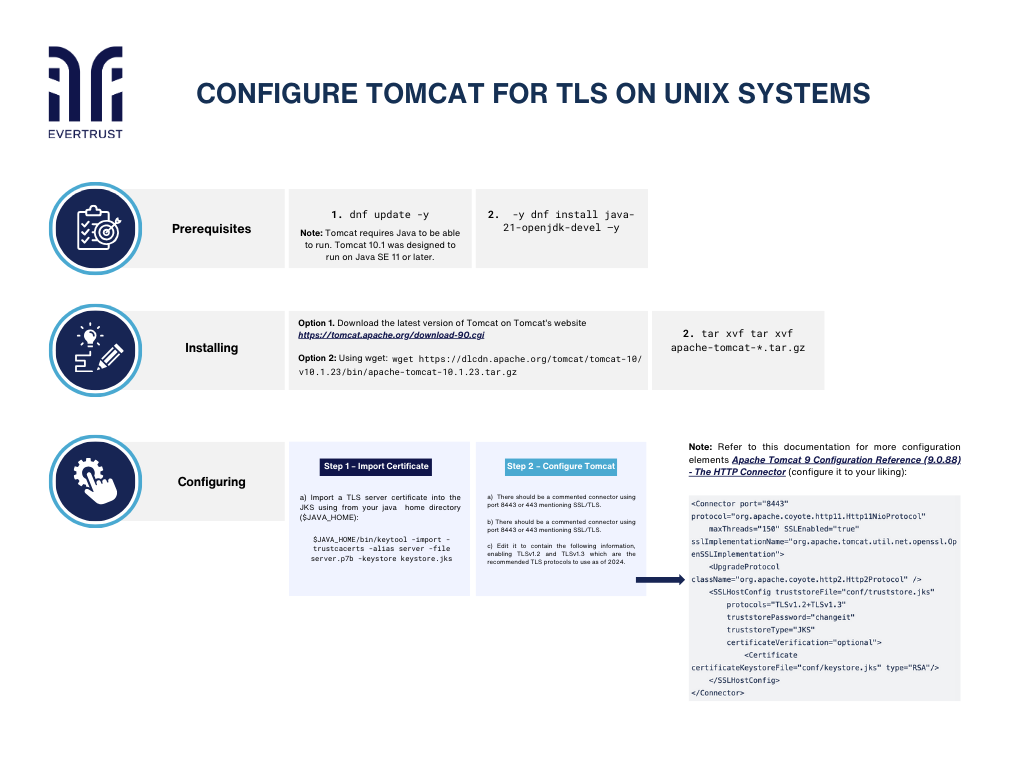 Configure Tomcat for TLS on UNIX systems
Configure Tomcat for TLS on UNIX systems
Therefore, here we present the fourth and final detailed guide in our sequence, in which we will provide you with the necessary knowledge and clear step-by-step instructions to establish a secure communication channel between your Tomcat server and your clients, allowing you to fortify your server against cyber threats.
But before diving into the configuration process, it is essential to ensure that the following prerequisites are met:
Start by updating system packages executing the following command:
dnf update -y
Note: Tomcat requires Java to be able to run. Tomcat 10.1 was designed to run on Java SE 11 or later.
To install the Java Development Kit (JDK), run the following command:
dnf install java-21-openjdk-devel –y
Download the latest version of Tomcat on Tomcat’s website (https://tomcat.apache.org/download-90.cgi) or using wget:
wget https://dlcdn.apache.org/tomcat/tomcat-10/v10.1.23/bin/apache-tomcat-10.1.23.tar.gz
Extract the downloaded file in a relevant directory such as /usr/local/tomcat10:
tar xvf tar xvf apache-tomcat-*.tar.gz
Step 1 – Import Certificate
a) To import a TLS server certificate into the Java Key Store (JKS), use the following command from your java home directory ($JAVA_HOME):
$JAVA_HOME/bin/keytool -import -trustcacerts -alias server -file server.p7b -keystore keystore.jks
Note: Stream and Horizon can be used to issue certificates. One of the use cases for said certificates is for TLS encryption for HTTPS communication over the internet. To enable TLS, it is mandatory to import the TLS certificate inside the keystore that will be used for Tomcat.
Step 2 - Configure Tomcat
a) To configure Tomcat for TLS encryption, edit the server.xml file under the conf directory.
b) There should be a commented connector using port 8443 or 443 mentioning SSL/TLS.
C) Edit it to contain the following information, enabling TLSv1.2 and TLSv1.3 which are the recommended TLS protocols to use as of 2024.
Note: Refer to this documentation for more configuration elements Apache Tomcat 9 Configuration Reference (9.0.88) - The HTTP Connector (configure it to your liking):
Note: Different types of keystores are configurable such as defined in Tomcat’s documentation: “In addition to the standard key store types (JKS and PKCS12), most Java runtimes support additional key store types such as Windows-ROOT, Windows-My, DKS as well as hardware security modules. “
Configuring TLS on UNIX systems for your Tomcat server is an essential step in securing your web applications and protecting sensitive data. By following the steps outlined in this guide, you've equipped yourself with the tools and knowledge needed to fortify your server against cyber threats effectively. Keep your configurations up to date and stay informed about emerging security standards to maintain a robust security posture.