Published on
April 2, 2024
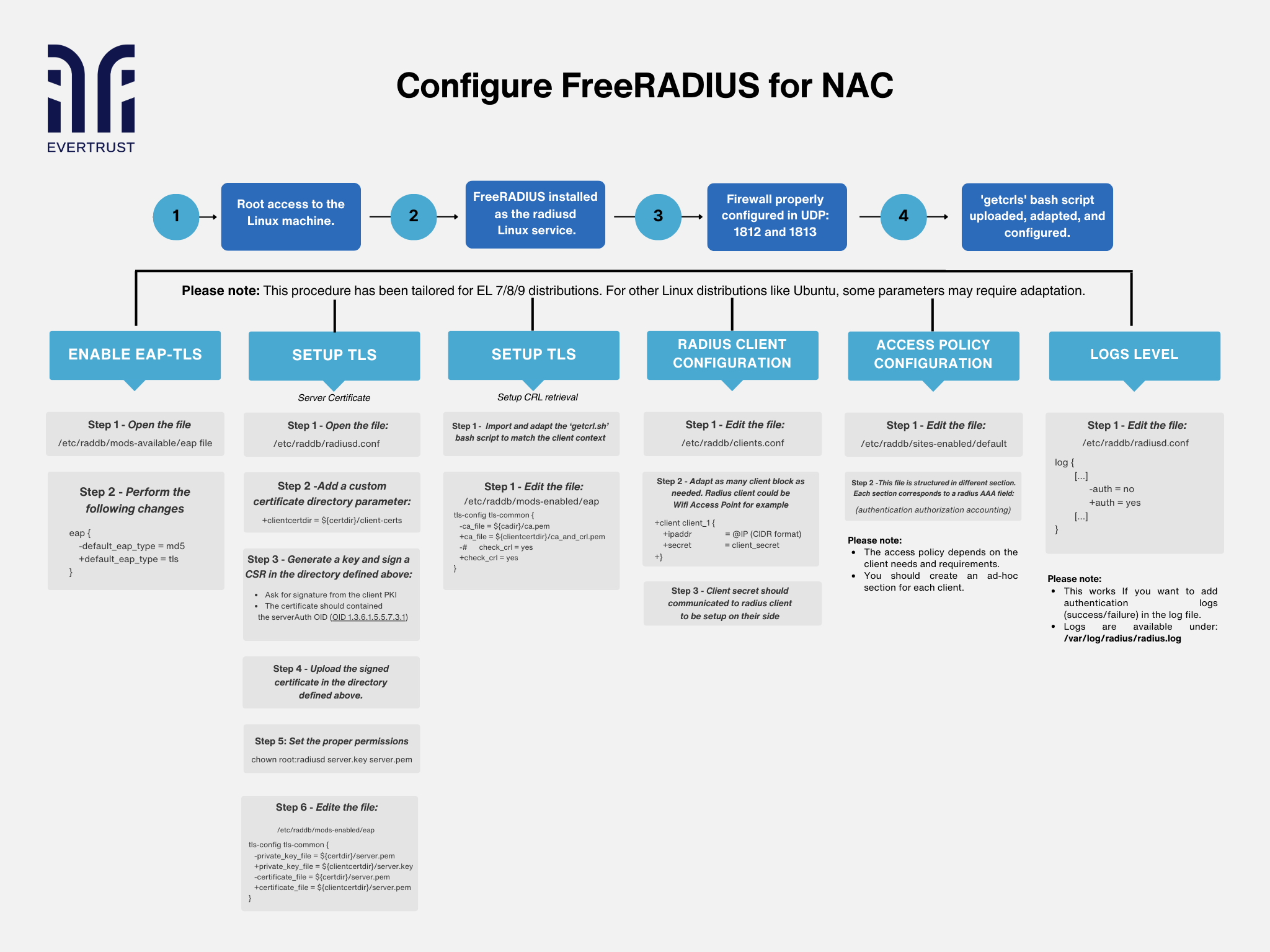
In today's digital landscape, ensuring robust network security is paramount for organizations of all sizes. Network Access Control (NAC) plays a crucial role in securing networks by regulating access based on predefined policies and in the following diagram we will guide you step-by-step through the process of configuring FreeRADIUS for NAC.
 Configure FreeRADIUS for NAC
Configure FreeRADIUS for NAC
But before diving into the configuration process, it is essential to ensure that the following prerequisites are met:
Prerequisites:
Root Access: Ensure root access to the Linux machine, granting necessary permissions for system-level configurations.
FreeRADIUS Installation: Install FreeRADIUS as a Linux service, commonly known as 'radiusd'.
Firewall Configuration: Open UDP ports 1812 and 1813 to allow communication for RADIUS authentication.
Upload and Configure 'getcrls' Script: Adapt and configure the 'getcrls' bash script to facilitate Certificate Revocation List (CRL) retrieval.
Please note: This procedure has been tailored for EL 7/8/9 distributions. For other Linux distributions like Ubuntu, some parameters may require adaptation.
Then,
To enable EAP-TLS authentication, follow these steps:
Open the '/etc/raddb/mods-available/eap' file.
Change the default EAP type to TLS within the configuration.
To set up TLS for secure communication, perform the following steps:
Open the '/etc/raddb/radiusd.conf' file.
Add a custom certificate directory parameter.
Generate a key, sign a Certificate Signing Request (CSR), and upload the signed certificate.
Want to implement these PKI practices?
Get expert guidance on implementing secure PKI solutions for your organization.
Get Expert HelpSet proper permissions for the server key and certificate files.
Edit the '/etc/raddb/mods-enabled/eap' file to configure TLS settings.
To configure Certificate Revocation List (CRL) retrieval as follows:
Import and adapt the 'getcrl.sh' bash script to match the client context.
Edit the '/etc/raddb/mods-enabled/eap' file to enable CRL checking.
To configure Radius client settings by:
Editing the '/etc/raddb/clients.conf' file.
Adapt client blocks as needed, providing IP addresses and secret keys.
To configure the access Policy:
Customize access policies based on client needs by editing the '/etc/raddb/sites-enabled/default' file.
Structure the file into sections corresponding to authentication, authorization, and accounting.
Finally, for logs level:
Enable authentication logs by modifying the '/etc/raddb/radiusd.conf' file.
Adjust logging parameters to specify which events should be recorded in the log file.
In conclusion, the meticulous implementation of FreeRADIUS on a Linux machine, following outlined procedures, significantly fortifies your organization's network security infrastructure. With robust authentication, authorization, and logging mechanisms established, secure access to network resources is assured while aligning with security policies.
By meticulously adapting procedures to specific Linux distributions, administrators effectively deploy FreeRADIUS for NAC, thereby enhancing network security and control. It's worth noting that while FreeRADIUS enables authentication of endpoints and users, issuing certificates for them is paramount. For this task, our solutions Horizon & Stream offer the most reliable and comprehensive approach.
 Horizon and Stream
Horizon and Stream